Explain Different Threats and Vulnerabilities Specific to Virtual Machines

Firewall Malwaredesign Data Loss Prevention Security Networking


The 6 Most Common Cyber Security Threats To Watch For In 2022
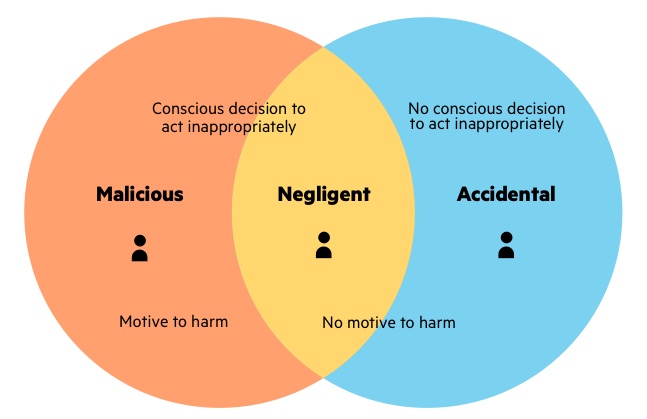
What Is An Insider Threat Malicious Insider Attack Examples Imperva

Security Threats And Risks In Smart Factories Nouvelles De Securite Trend Micro Fr
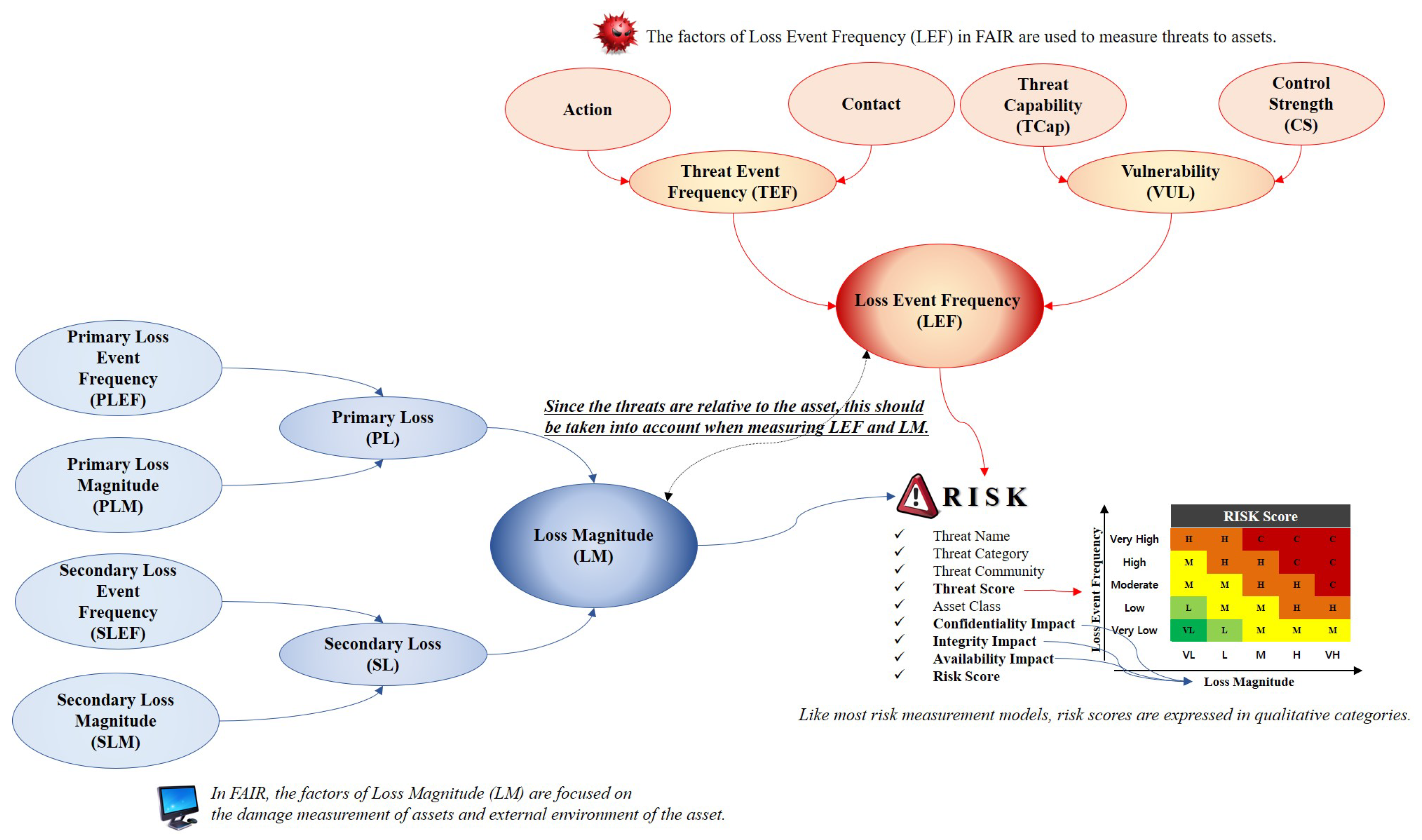
Sensors Free Full Text Security Risk Measurement For Information Leakage In Iot Based Smart Homes From A Situational Awareness Perspective Html
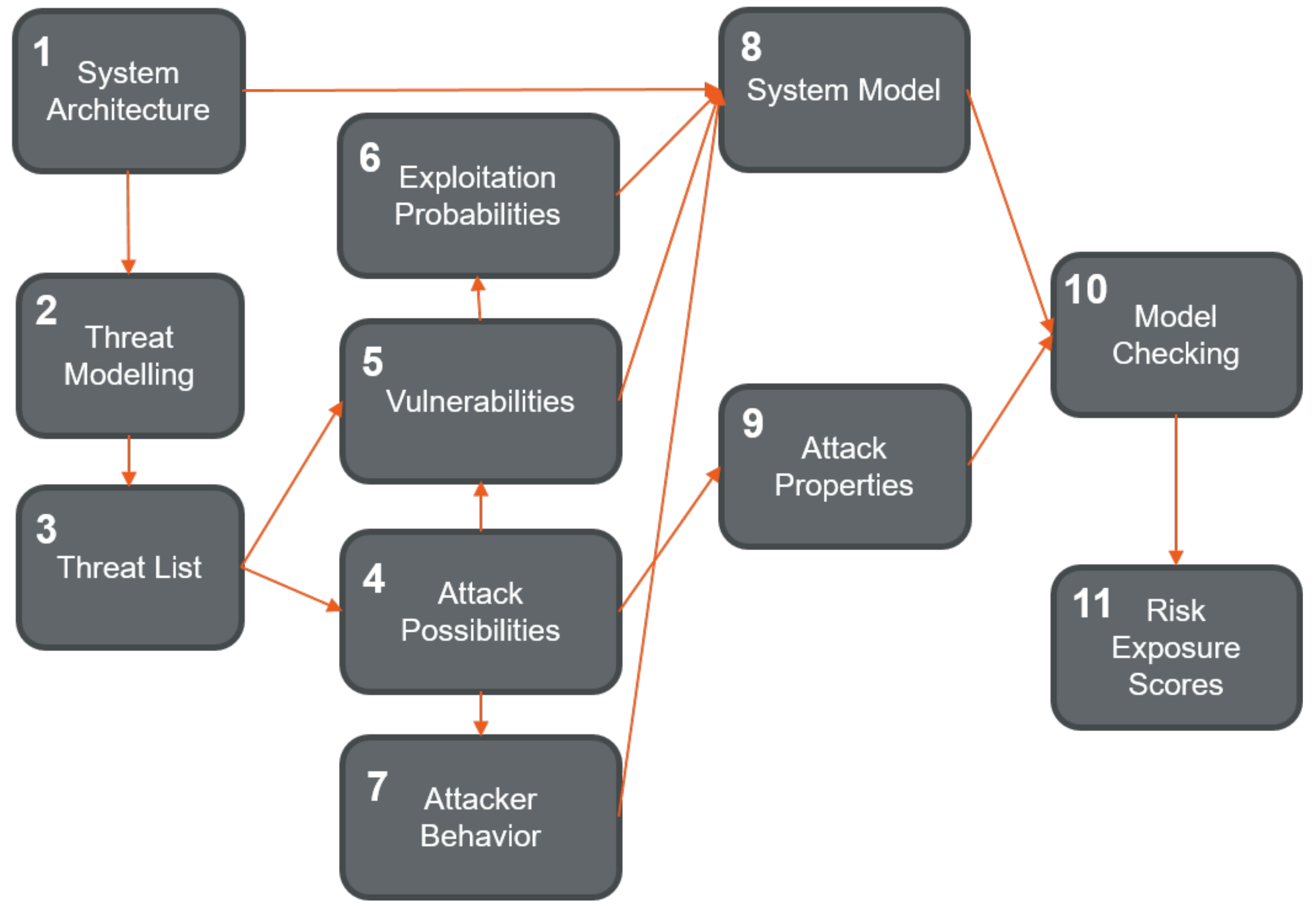
Applied Sciences Free Full Text Threat Modelling And Beyond Novel Approaches To Cyber Secure The Smart Energy System Html
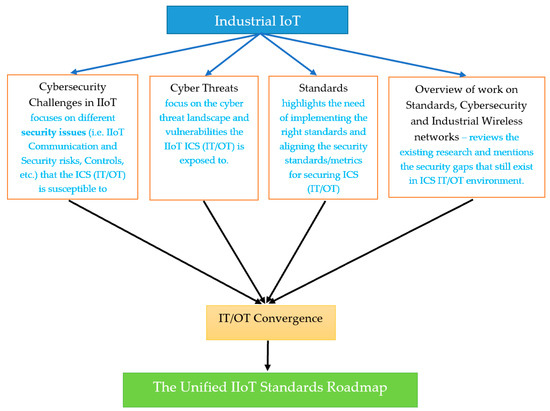
Sensors Free Full Text Industrial Iot Cyber Threats And Standards Landscape Evaluation And Roadmap Html

2022 Guide To Cyber Threat Detection And Response Tdr

Top 8 Mobile Threats Risks In 2021 What Mnos Can Do Firstpoint

Rising Cybersecurity Threats Expected To Continue In 2022 Global X Etfs

It Security Vulnerability Vs Threat Vs Risk What Are The Differences Bmc Software Blogs

Pdf Analyzing Security Threats To Virtual Machines Monitor In Cloud Computing Environment

Mobile Security Tips Mobile Security Computer Security Security Tips

Network Security Threats 5 Ways To Protect Yourself

Pdf Cyber Security Threats And Vulnerabilities A Systematic Mapping Study

Gsma Fs 33 Network Function Virtualisation Nfv Threats Analysis Security
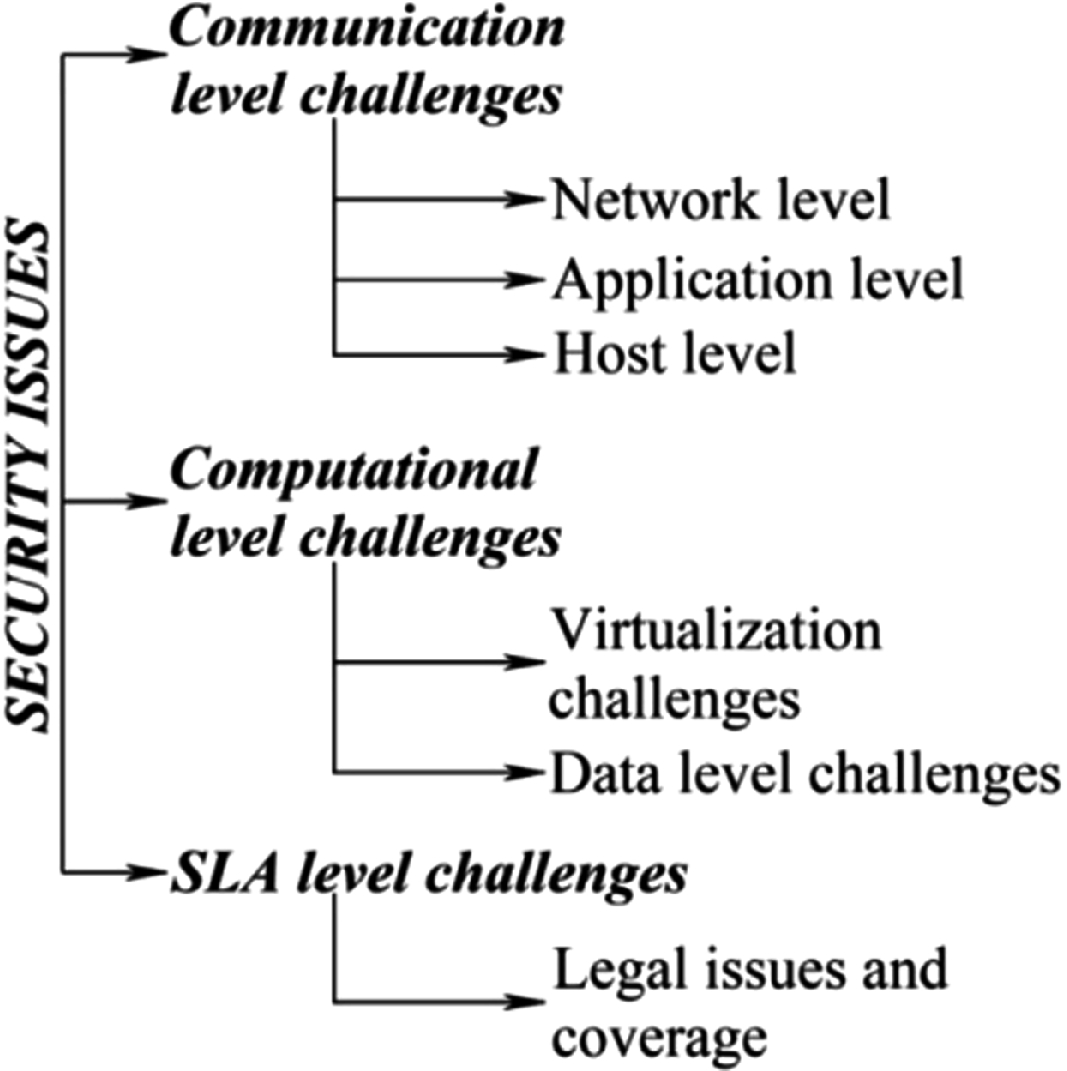
Exploration Of Various Cloud Security Challenges And Threats Springerlink
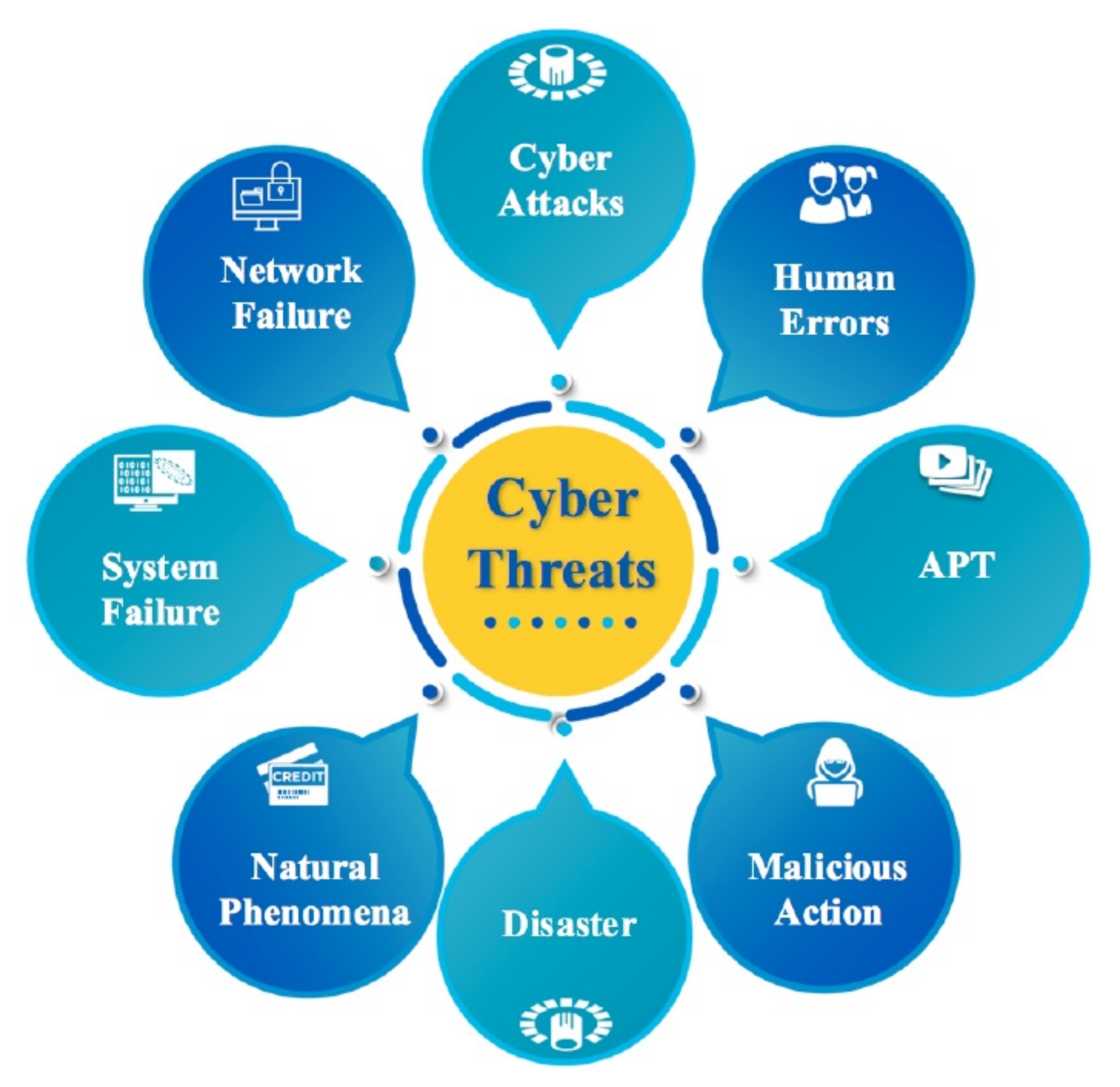
Applied Sciences Free Full Text Internet Of Things Meet Internet Of Threats New Concern Cyber Security Issues Of Critical Cyber Infrastructure Html

Comments
Post a Comment